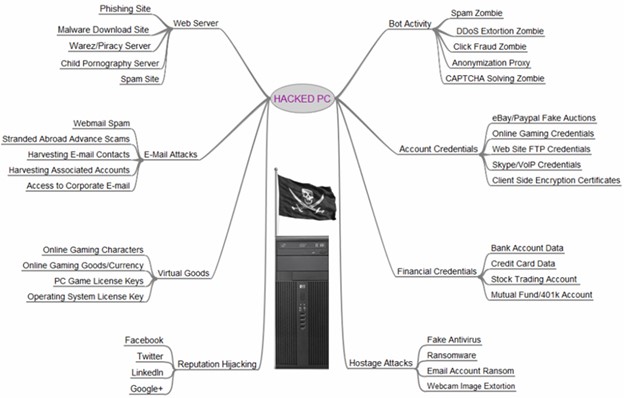
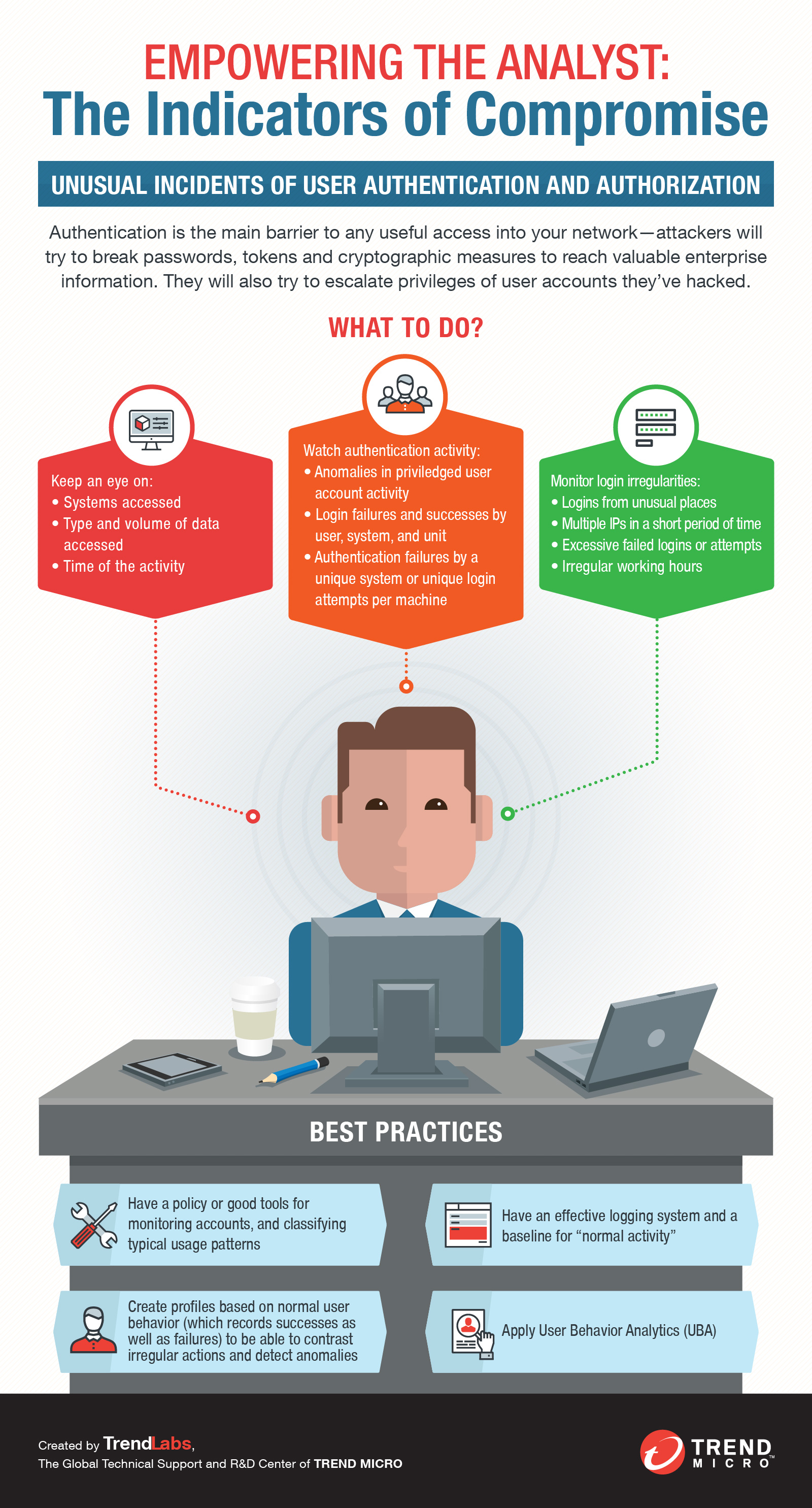
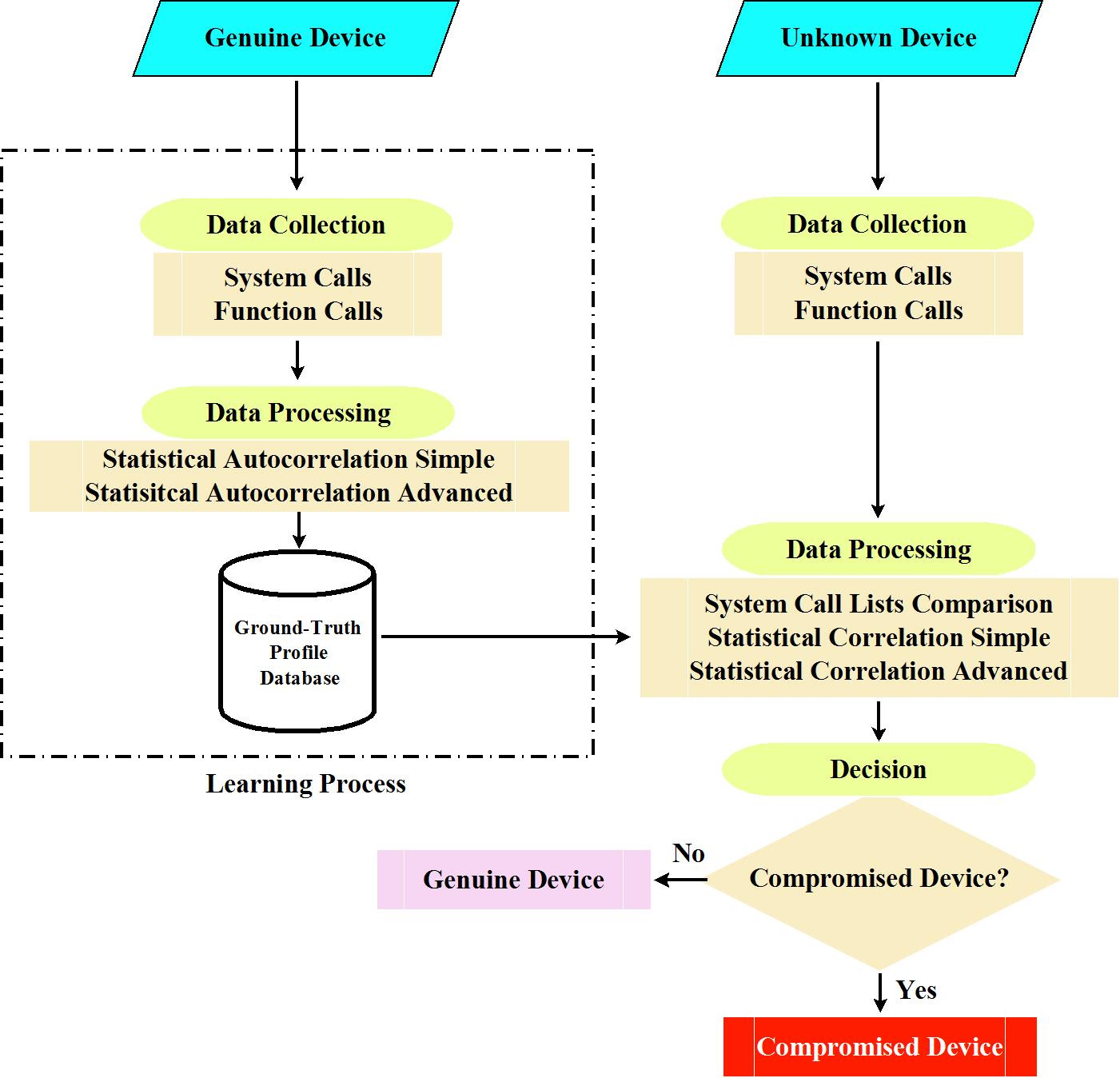
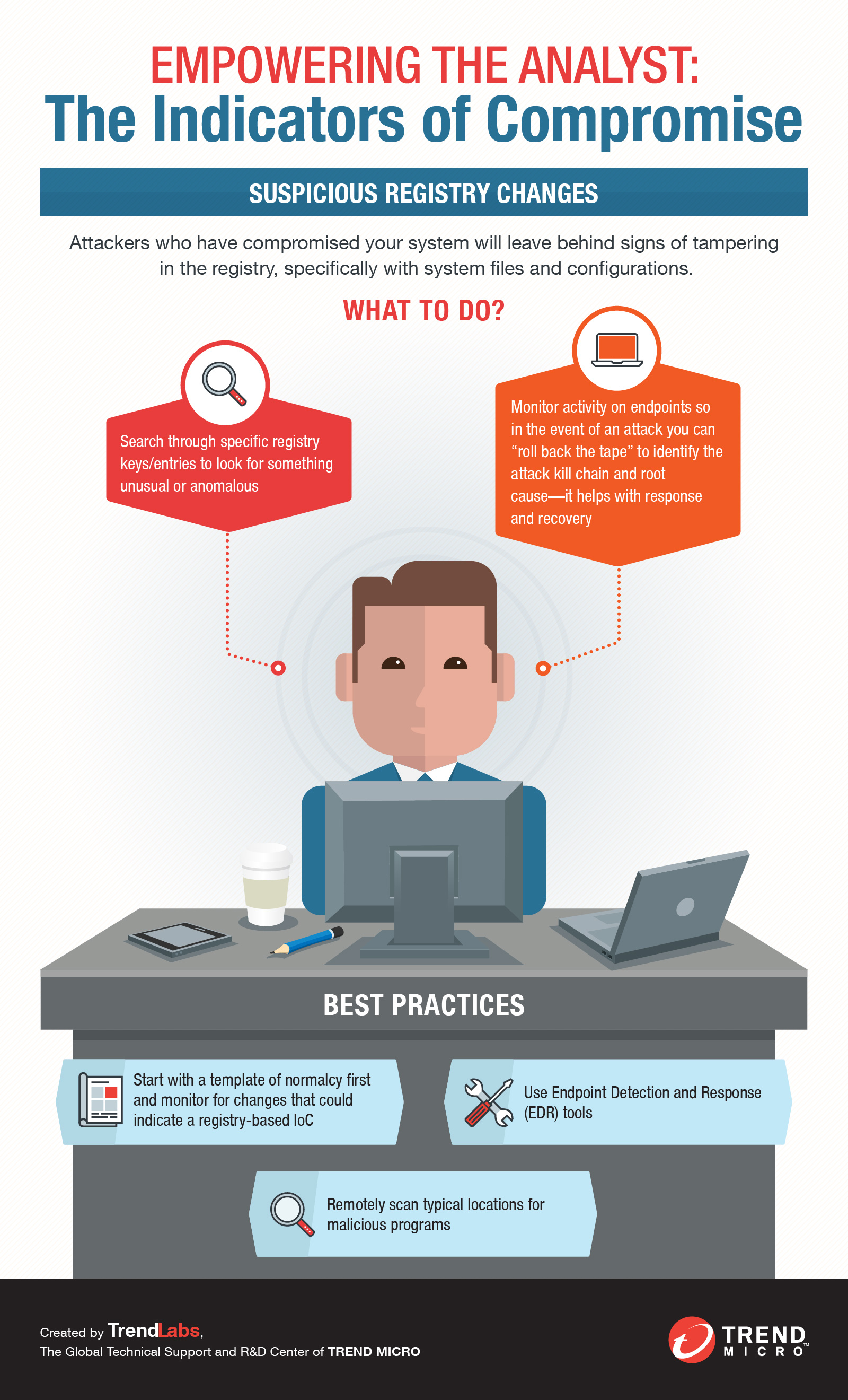
System hacked alert after cyber attack on taplet network. compromised information concept. internet virus cyber security and cybercrime.. 素材庫相片| Adobe Stock

System hacked warning alert on notebook (Laptop). Cyber attack on computer network, Virus, Spyware, Malware or Malicious software. Cyber security and cybercrime. Compromised information internet. Photos | Adobe Stock