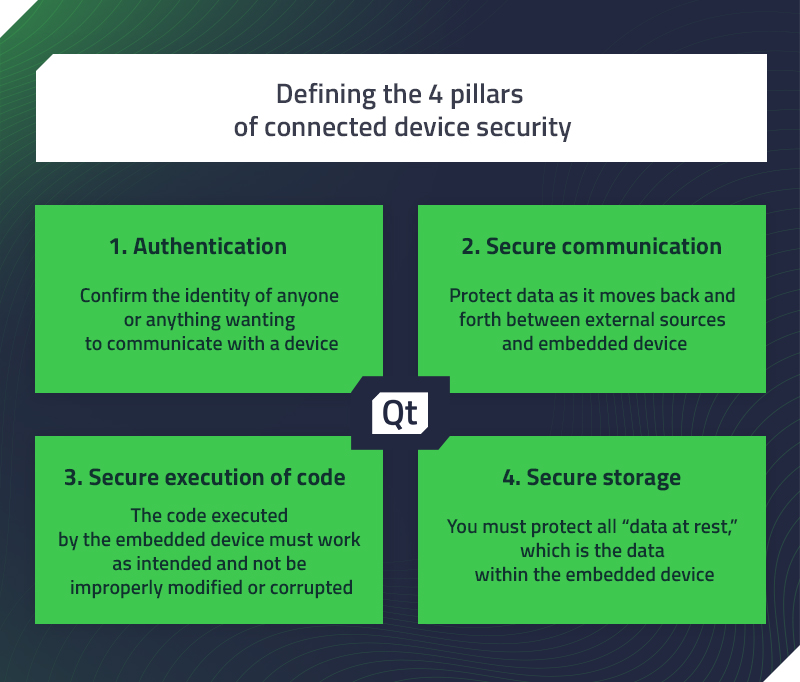
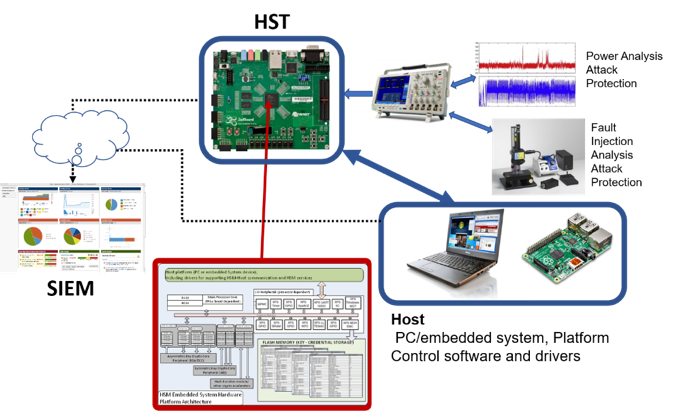
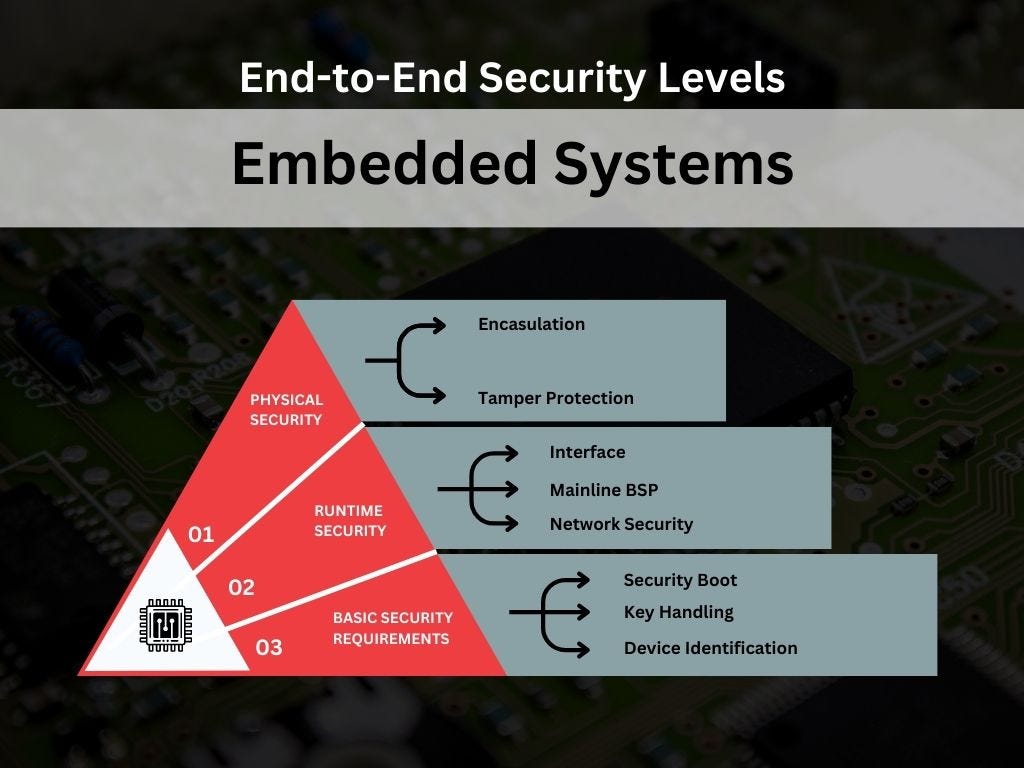
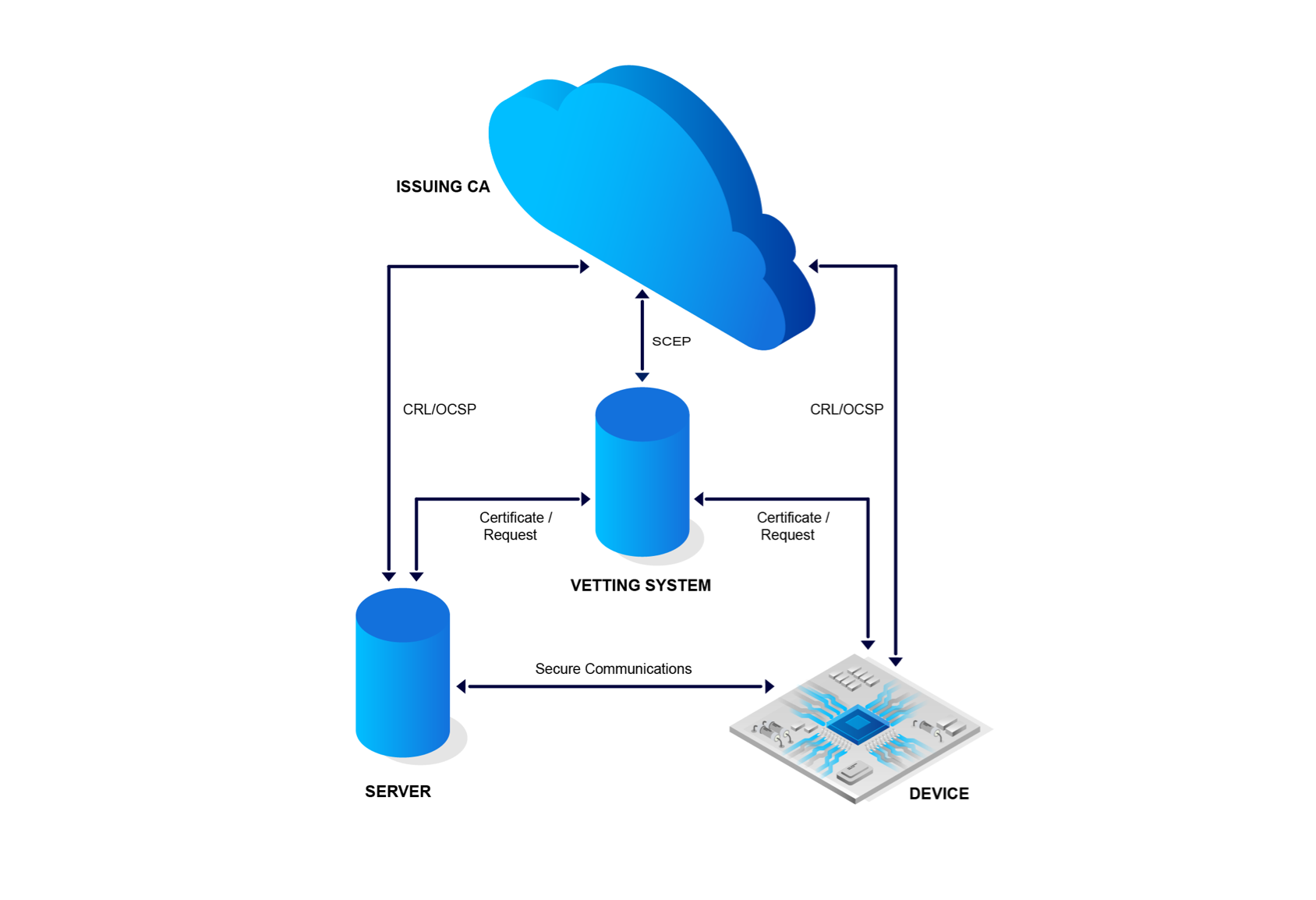
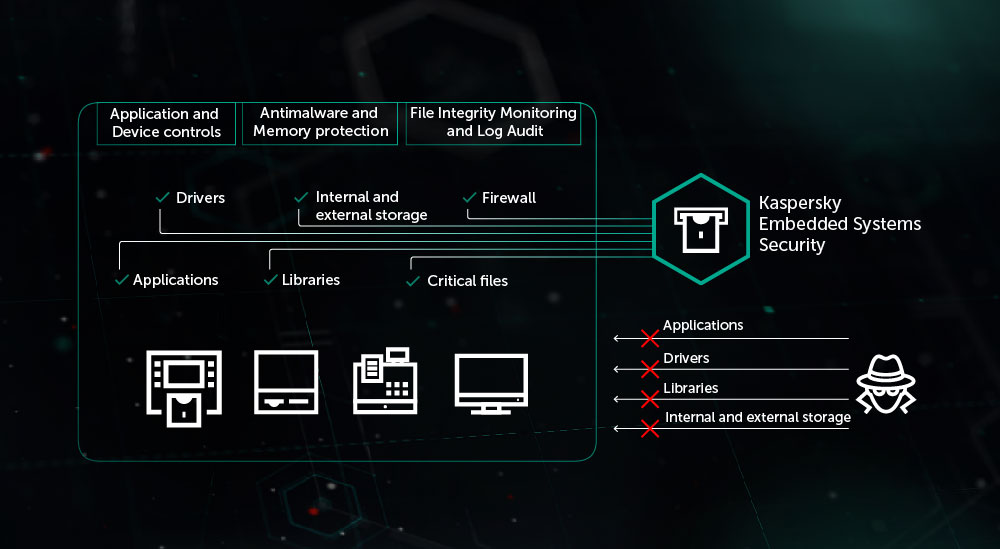
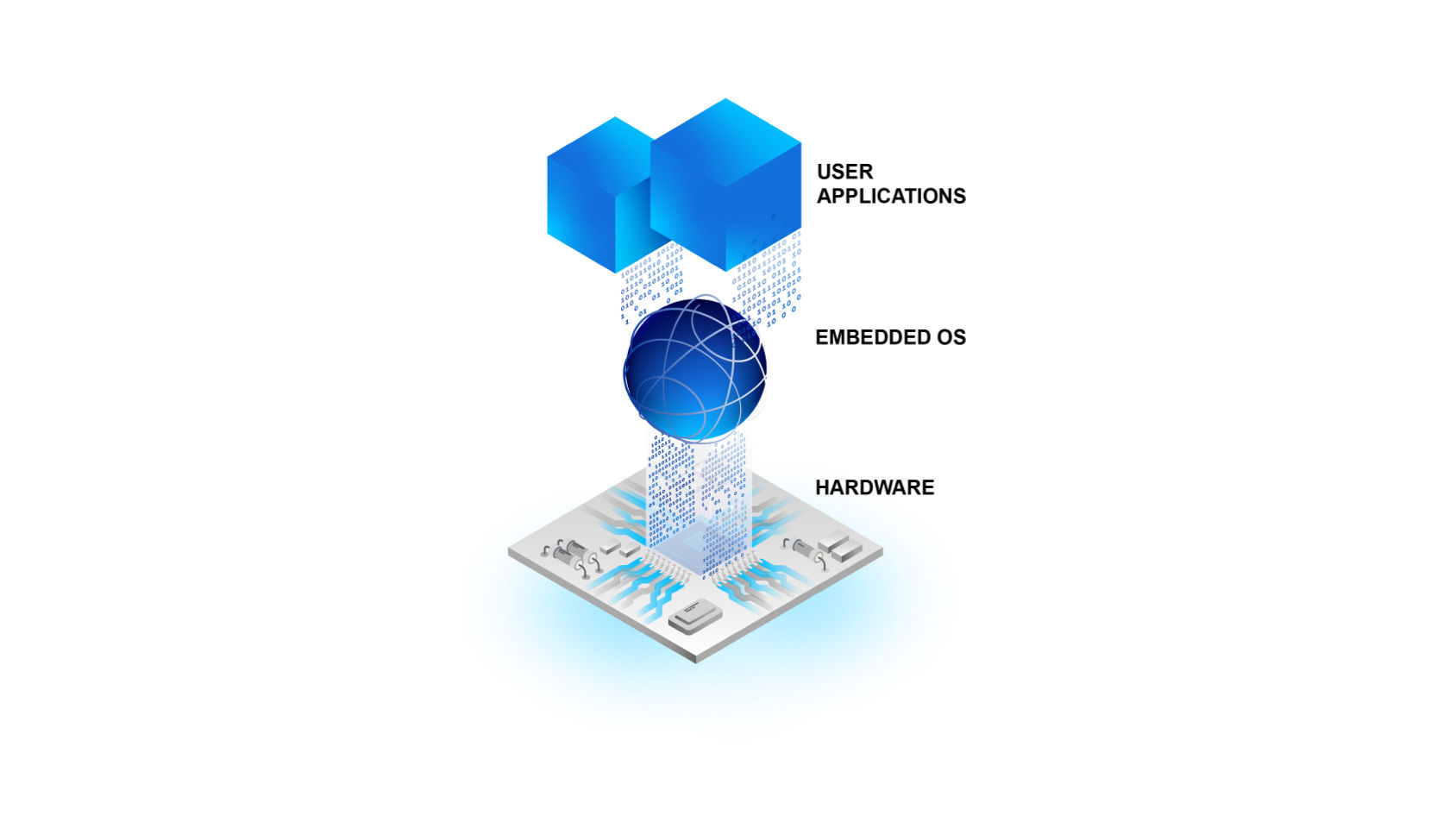
Why do you need a hardware solution to secure your embedded system? — Silex Insight Technical Article | ChipEstimate.com
Embedded Systems Cybersecurity Regulations: How Legislation Is Responding to Security Threats | Digi International

Future Electronics — How to Maximize Embedded System Security and Prevent Cyber Attacks | Futureelectronics NorthAmerica Site

Amazon.fr - Embedded Systems Security: Practical Methods for Safe and Secure Software and Systems Development - Kleidermacher, David, Kleidermacher, Mike - Livres


.jpg?lang=en-US&width=700&height=697)